Kerberos single sign-on with SSH v2 under windows
Using Kerberos it is possible to "kerberize" services and applications to enhance security. Compared to classical username/password authentification Kerberos uses time-limited tickets which are applied per-user for authentificating against services and applications.
In combination with SSH the encrypted remote protocol can be further secured - who worries about security (or seems to be paranoid) can force using Kerberos authentification instead of conventional authentification using the following changes to the SSH server configuration (/etc/ssh/sshd_config):
1#PermitRootLogin yes
2PermitRootLogin no
3...
4#PasswordAuthentication yes
5PasswordAuthentication no
6...
7#KerberosAuthentication no
8KerberosAuthentication yes
9...
10#GSSAPIAuthentication no
11GSSAPIAuthentication yes
12#GSSAPICleanupCredentials yes
13GSSAPICleanupCredentials yes
After a restart of the ssh service only Kerberos user are allowed, root isn't allowed to login anymore (which is also a good security enhancement!).
From an appropriate certified Linux host it is possible to login using a valid Kerberos username.
Unfortunately this isn't that easy under Windows because it doesn't use "plain" MIT Kerberos. No problem, there is an software package by MIT for Windows available: MIT Kerberos for Windows (make sure you install version 3.2.2 and not 4.0!).
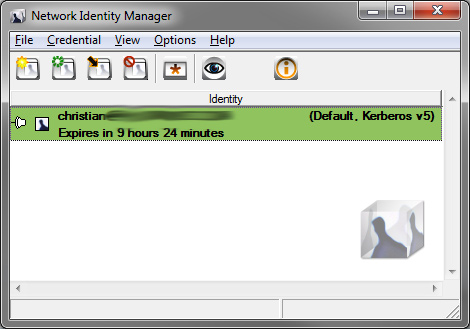
This software package delivers the needed libraries and a tool named "Network Identity Manager". Using this tool Kerberos tickets are requested, listed and deleted - the equivalent to the kinit / klist / kdestroy utilities.
It is important to start this tool for the first time after the installation as administrator. This is necessary to delete the preconfigured Kerberos REALM and setup the custom Kerberos configuration. After this, the tool can be used with classical permissions.
Using a graphical assistant the needed Kerberos information (KDC, admin server, REALM) are configured in a few moments.
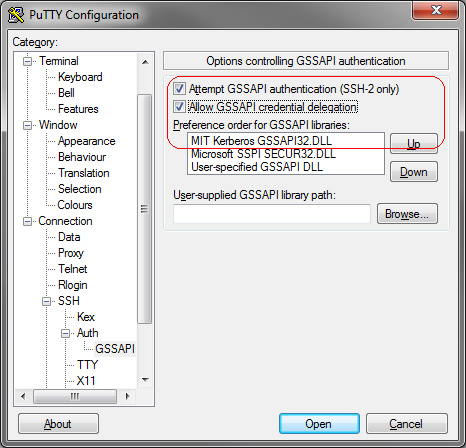
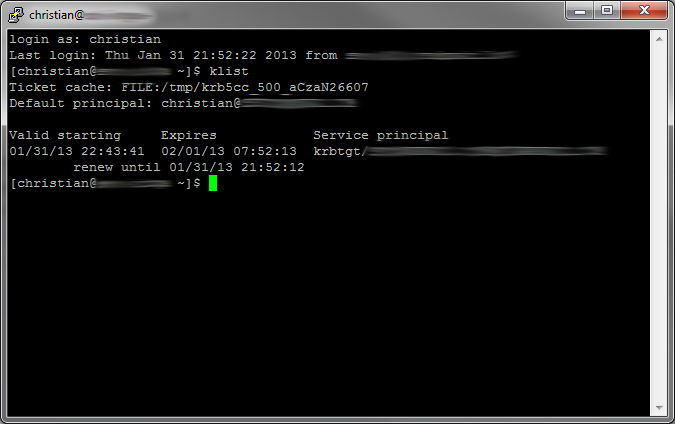
After creating the configuration, it is necessary to activate GSSAPI authentification in PuTTy (which required at least version 0.6.2). If a valid Kerberos ticket is cached, the login is processed without typing a password after entering the proper username (see screenshot).