Microsoft Active Directory Domain Services authentification under VMware vCenter Server Appliance 6
For integration in Microsoft environments, VMware offers several Microsoft Active Directory Domain Services (AD DS) connectors in vCenter Server:
- native integration: vCenter Server is managed as computer object in Active Directory
- LDAP broker for authentification in Single-Sign-On (SSO)
When installing the last vCenter Server 5.x update (5.5U3) I saw that this integration seems to be unreliable. I often had the issue that authentification was not working anymore - even without changing the environment. The log files did not help at all; re-joining the vCenter Server into Active Directory helped a several times with fixing the issue.
It seems like this problem still exists in vCenter Server Appliance 6.0U1. Therefore, I decided to go for the LDAP integration for authenticating directory users for vCenter Server. Configuring the appropriate identity resources failed even though the connection test was successful. Unfortunately, the log file /var/log/vmware/sso/ssoAdminServer.log did not help with troubleshooting:
1[2015-11-12T09:31:56.743Z pool-2-thread-3 opID=...] Registering a new Ldap identity source of type 'Active Directory' with name 'mycompany.mydomain.loc' and alias 'mycompany'
2[2015-11-12T09:31:56.743Z pool-2-thread-3 opID=...] Failed to probe provider connectivity [URI: ldap://mydc.mycompany.mydomain.loc:389]; ...
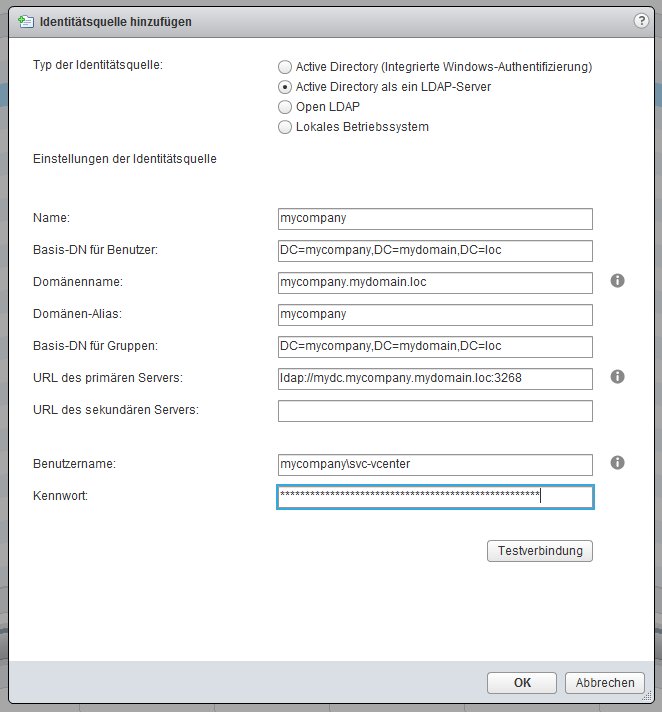
After some additional tests, I found out that some things need to be considered during configuration:
- The username needs to be specified along with the domain short name
- Don't specify a secondary server, don't use port 389
I don't know whether this needs to be considered generally; but it was necessary for my Windows Server 2008 R2 lab.
The working configuration for my lab (Domain mycompany.mydomain.loc, DC mydc.mycompany.mydomain.loc) looks like this:
| Setting | Explanation/Value |
|---|---|
| Name | Short description, e.g. domain short name: mydomain |
| Base DN for users | DC=mycompany,DC=mydomain,DC=loc |
| Domain name | mycompany.mydomain.loc |
| Domain alias | mycompany |
| Base DN for groups | DC=mycompany,DC=mydomain,DC=loc |
| Primary server URL | LDAP URL with port 3268 instead of 389: ldap://mydc.mycompany.mydomain.loc:3268 |
| Secondary server URL | <empty> |
| Username | Service user for reading the directory, use domain short name: mycompanyusername |
| Password | <password> |