Authenticate Spacewalk users with FreeIPA
A fresh Spacewalk installation usually defines user accounts in a local manner - including permissions. Especially for bigger system landscapes with requirements such as Single Sign-on, this is not a practical solution.
Fortunately, Spacewalk and Red Hat Satellite 5 support authentication using FreeIPA and Red Hat Identity Management. Beginning with Spacewalk 2.3 and Red Hat Satellite 5.7 there is an utility called spacewalk-setup-ipa-authentication which fully automates configuration all participating components (SSSD, Apache, Tomcat, SELinux). Prior to those versions, changes need to be made manually.
Preparation
First of all, an appropriate Kerberos service specifying the Spacewalk server's FQDN needs to be created. To ensure this, open the FreeIPA web interface and click Identity > Services > Add:
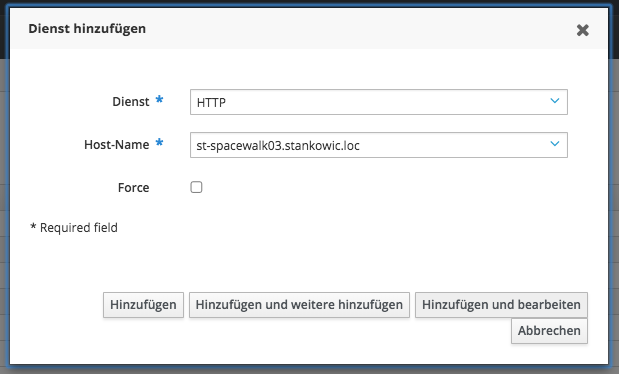
Alternatively, create the service using a registered system by utilizing the ipa command with a specified administrator Kerberos ticket:
1# kinit admin
2# ipa service-add HTTP/spacewalk-fqdn
Afterwards it is a good idea to create user groups in FreeIPA for the Spacewalk accounts and their required permissions. For this, click Identity > User Groups > Add nötig. Spacewalk supports the following roles:
- Administrative roles (system-wide)
- Organisation administrator
- Spacewalk administrator
- Roles
- Activation key dministrator (per organisation)
- configuration administrator (client configuration files)
- channel administrator
- system group administrator
In a next step, these FreeIPA groups are assigned to the appropriate roles inside Spacewalk. Depending on your use-case it might be a good idea to create multiple groups - e.g. a group for all Spacewalk-wide administrators:
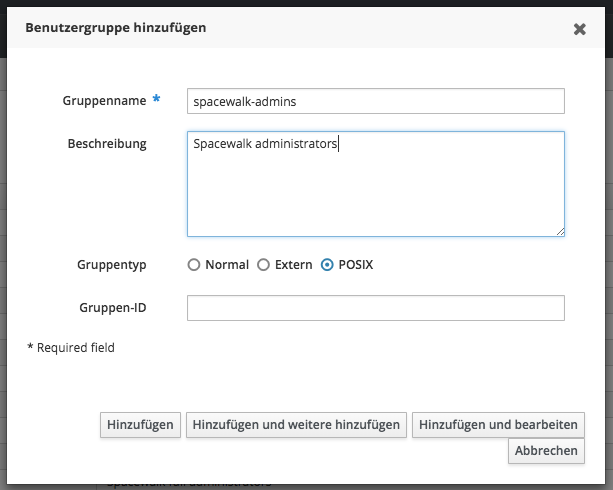
Of course, there is also an ipa command for that:
1# ipa group-add spacewalk-admins --desc "Spacewalk administrators"
Configuration
The next step is to configure IPA authentication on the Spacewalk system:
1# spacewalk-setup-ipa-authentication
2Enabling authentication against [pinkepank.stankowic.loc].
3Retrieving HTTP/ service keytab into [/etc/httpd/conf/http.keytab] ...
4Keytab successfully retrieved and stored in: /etc/httpd/conf/http.keytab
5changed ownership of `/etc/httpd/conf/http.keytab' to apache
6Configuring PAM service [spacewalk].
7Will install additional packages ...
8
9** /etc/sssd/sssd.conf has been backed up to sssd.conf-swsave
10Updated sssd configuration.
11Turning SELinux boolean [httpd_dbus_sssd] on ...
12 ... done.
13Turning SELinux boolean [allow_httpd_mod_auth_pam] on ...
14 ... done.
15Configuring Apache modules.
16** /etc/tomcat6/server.xml has been backed up to server.xml-swsave.ipa
17Stopping sssd: [ OK ]
18Starting sssd: [ OK ]
19Stopping tomcat6: [ OK ]
20Starting tomcat6: [ OK ]
21Stopping httpd: [ OK ]
22Starting httpd: httpd: [ OK ]
23Waiting for tomcat to be ready ...
24Authentication against [pinkepank.stankowic.loc] sucessfully enabled.
25As admin, at Admin > Users > External Authentication, select
26 Default organization to autopopulate new users into.
Afterwards, a default organization for FreeIPA users that have never logged in into Spacewalk needs to be configured. For this, open the Spacewalk web interface and click Admin > Users > External Authentication.
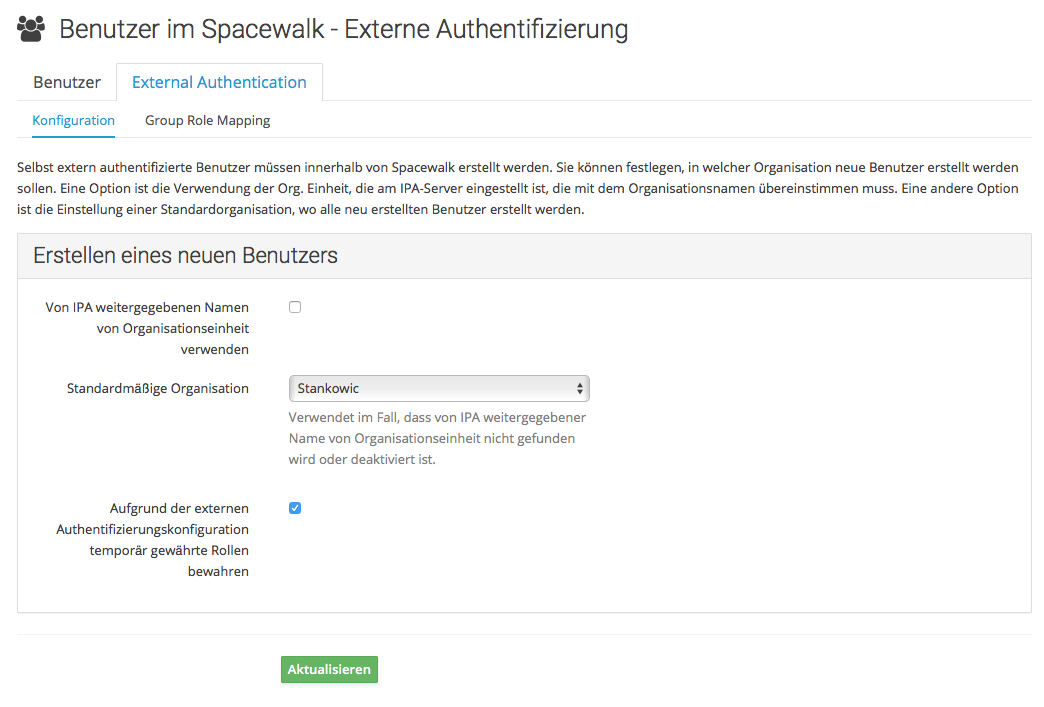
If organizations in Spacewalk match those defined in FreeIPA, check "Use organization unit name passed from IPA". If names differ, it is possible to define a default organization next to "Default Organization". Make sure to check "Keep temporary roles granted due to external authentication configuration" in any case as otherwise group memberships in FreeIPA won't trigger permissions in Spacewalk.
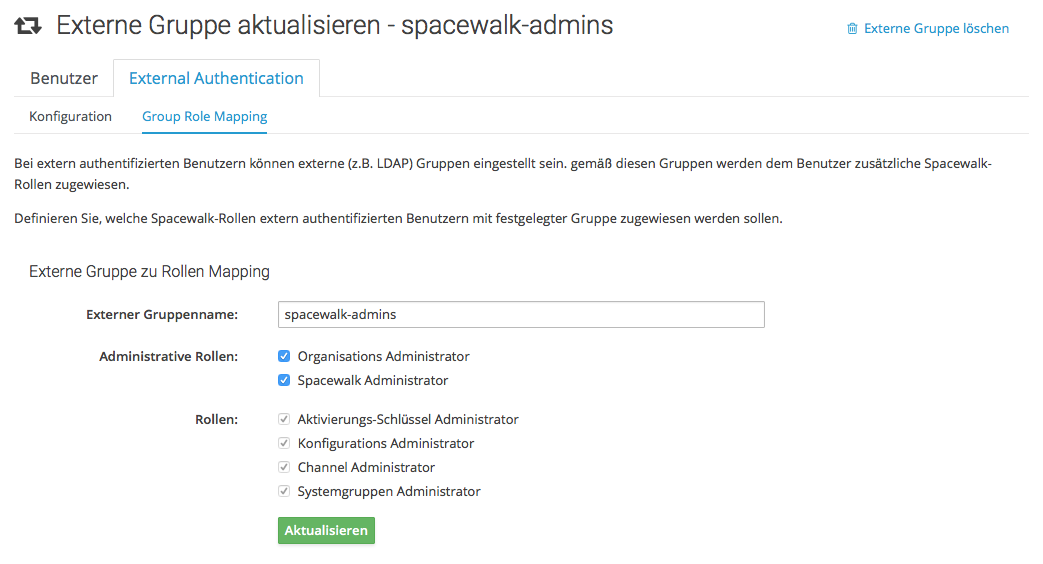
Group and role memberships are defined in the Group Role Mapping pane:
Depending on the Spacewalk patch level it might be necessary to restart the service before authentication works:
1# spacewalk-service restart