Red Hat Summit 2024
From 06.05 to 09.05 the Red Hat Summit took place in Denver. The conference once again focused on the latest developments and announcements from the company's own ranks. Approximately 6000 participants attended the event in Colorado.
On the occasion of the Red Hat Summit 2024, a two-part special was published in the FOCUS ON: Linux podcast. In addition to a wrap-up, there are also numerous interviews with experts.
Location
The event took place in the almost 20-hectare Colorado Convention Center - the number of hands-on labs, presentations and workshops on offer rose to 485. Compared to last year, it was even easier to get lost - the Red Hat Event Guide app was absolutely necessary to find your way around. Visitors were well advised to reserve desired lectures in advance in the schedule - lecture rooms and waiting lists were quickly exhausted. In the exhibition area there were community stands (e.g. Ansible, CentOS, Fedora) as well as numerous manufacturers who answered questions and also presented new products.






At one of the numerous Red Hat booths, caps could be customized with product logos, the Red Hat video team had a full recording studio for interviews and demos. There were also book signing sessions again. In addition to countless stickers and other giveaways, this time there were also two pickleball courts for sporting activities. There was also a dog petting zoo - a nice idea in principle, but unfortunately not all visitors knew how to treat the animals with respect.
Also entertaining was an escape room, in which - to my surprise - it was not about leaving the editor vim. Instead, common elements of exit rooms were brought into the Red Hat context. Unfortunately, our group just missed the time limit.




The Big Blue Bear statue "I See What You Mean" in front of the Colorado Conference Center was created by Lawrence Argent, is 12 meters high and weighs 5 tons. It alludes to the wildlife in the immediate vicinity and picks up on a local news story in which a bear peered through the window of a residential building.
Keynotes
Like last year, the conference was all about AI ✨🚀. The topic seems to be a perennial favorite across all industries and, in my observation, needs to be incorporated into current tools - even if it doesn't always promise concrete benefits.
Matt Hicks (President and CEO, Red Hat) set the conference theme in the first keynote "Unleashing the Power of Hybrid Cloud and AI". Artificial intelligence is now at a level where standard hardware, rather than exotic hardware, is sufficient to consume and train AI models. After Meta became the first company to offer open source AI models, IBM and Red Hat cooperated to offer the Granite model family under the free Apache license. However, while the Mistral and Llama 2 models are difficult to access, Red Hat plans to radically simplify the training of models. To this end, the InstructLab project was presented, which I will discuss in more detail in a moment.
In conclusion, Hicks summarized that AI is - even if some are still sceptical - a technology that is here to stay. And in this case, an open-source solution should always be preferred to a proprietary one.
In the second keynote "Optimizing IT Infrastructure for the AI Era", RHEL Lightspeed, a chatbot under development for the in-house Linux distribution, was teased. It is intended to be equally useful for newcomers and experts. When used in everyday situations, it should provide useful tips and be able to answer even complex questions. What the implementation might ultimately look like was left open - personally, I'm thinking of an additional feature for Red Hat Insights.



The AnsibleFest keynotes "Automation, AI, and the next enterprise IT revolution" and "Adopting a mission-critical automation mindset" once again reported on Ansible Lightspeed, which was first introduced last year. Within a year, the model was upgraded so that it can now also generate complete playbooks instead of individual tasks.
A chatbot interface was demonstrated, which suggested several tasks from a description and then inserted them into a development environment. Another new feature is the ability to explain existing code - this function should make it easier for newcomers in particular to get started. The training was based on validated partner content from the Red Hat Automation Hub and Ansible Galaxy content with a high quality ranking.
In another keynote, a fully automated troubleshooting of a fictitious distribution company was demonstrated. Here, Event-driven Ansible and Ansible Lightspeed were used to analyze Windows event log errors (a subtle side-swipe? 😼) and turn potential countermeasures into code. This code was then automatically integrated and executed using Git version control. Technically certainly impressive, but in my opinion completely unimaginable in production environments.
All in all, I found the keynotes less technical and much more superficial compared to last year. The only exception was the live demo by InstructLab and Podman AI Lab, in which an AI model was adapted locally with a few tricks and then transferred to an OpenShift cluster. It remains to be seen whether the AI hypetrain will level off next year.



InstructLab
InstructLab (Large-scale alignment for Chatbots) received the most media attention. This is a community project that aims to greatly simplify the use and adaptation of generative AI models (Gen AI). While these tasks were previously mainly attributed to data scientists and AI developers, developers with less prior knowledge should also be able to perform them in the future.
Gen AI describes AI models that can generate individual content such as source code, text or images in response to a prompt ("Write me a Hello World in Python").
The basis of common Gen AI solutions is the use of so-called Large Language Models (LLMs) - i.e. powerful language models that are able to understand and generate human language. Representatives such as openAI GPT-3, for example, are able to understand and summarize the content of complex texts.
The project currently consists of a command line application, which enables the expansion of predefined models using simple YAML documents, in which so-called taxonomies and skills are defined. InstructLab is compatible with the top dog openAI and supports the import of your own models in GGUF format. Numerous examples should make it easier to get started.
Podman AI Lab extends Podman Desktop with the functionality to develop and execute LLMs locally - under Linux, macOS and Windows.
With RHEL AI, a RHEL variant specially optimized for the development and use of Gen AI models was introduced. This can be run on conventional PC hardware as well as on Edge devices and fully-fledged OpenShift clusters.
Ansible Automation Platform 2.5
I am looking forward to the next Ansible Automation Platform (AAP) version 2.5 in coming July. This will come with a greatly improved UX - whereby the highlight is likely to be a modular central web interface. This combines the previously dedicated interfaces of the Automation Controller, Private Automation Hub and the Event-driven Ansible Controller. A gateway service was developed for this purpose, which recognizes the components actually used and lists them accordingly in the navigation. AAP can be implemented as clearly or complexly as desired and a uniform web interface is an improvement that I have been waiting for. The development was the result of specific user feedback - an upgrade from version 2.4 will be possible.
Another improvement is that the view varies depending on the role of the logged-in user. The focus of the displayed elements differs between the Admin, Developer and Operator roles. The view will also be customizable with regard to some parameters (including theme, time and automatic refresh of the displayed information). Another new feature is a frequently requested dark mode. In a conversation with one of the developers, I was able to see the current status for myself. The concept is convincing and I'm already looking forward to using the new version myself.
As a side note, it was noted that new AAP versions will in future only be released only annually in order to reduce the maintenance effort. A sensible decision in my opinion, as updating complex environments can sometimes take a lot of time.
Another highlight was the preview of a new feature called Automated Policy as Code. This is intended to link workflow execution within AAP to further conditions in order to ensure compliance with policies. However, this does not necessarily mean security, as three examples from a keynote showed.
So-called policybooks were defined here, which checked playbooks with regard to their execution time, collections used or role parameters - for example, to ensure validated code or reduce cloud costs.

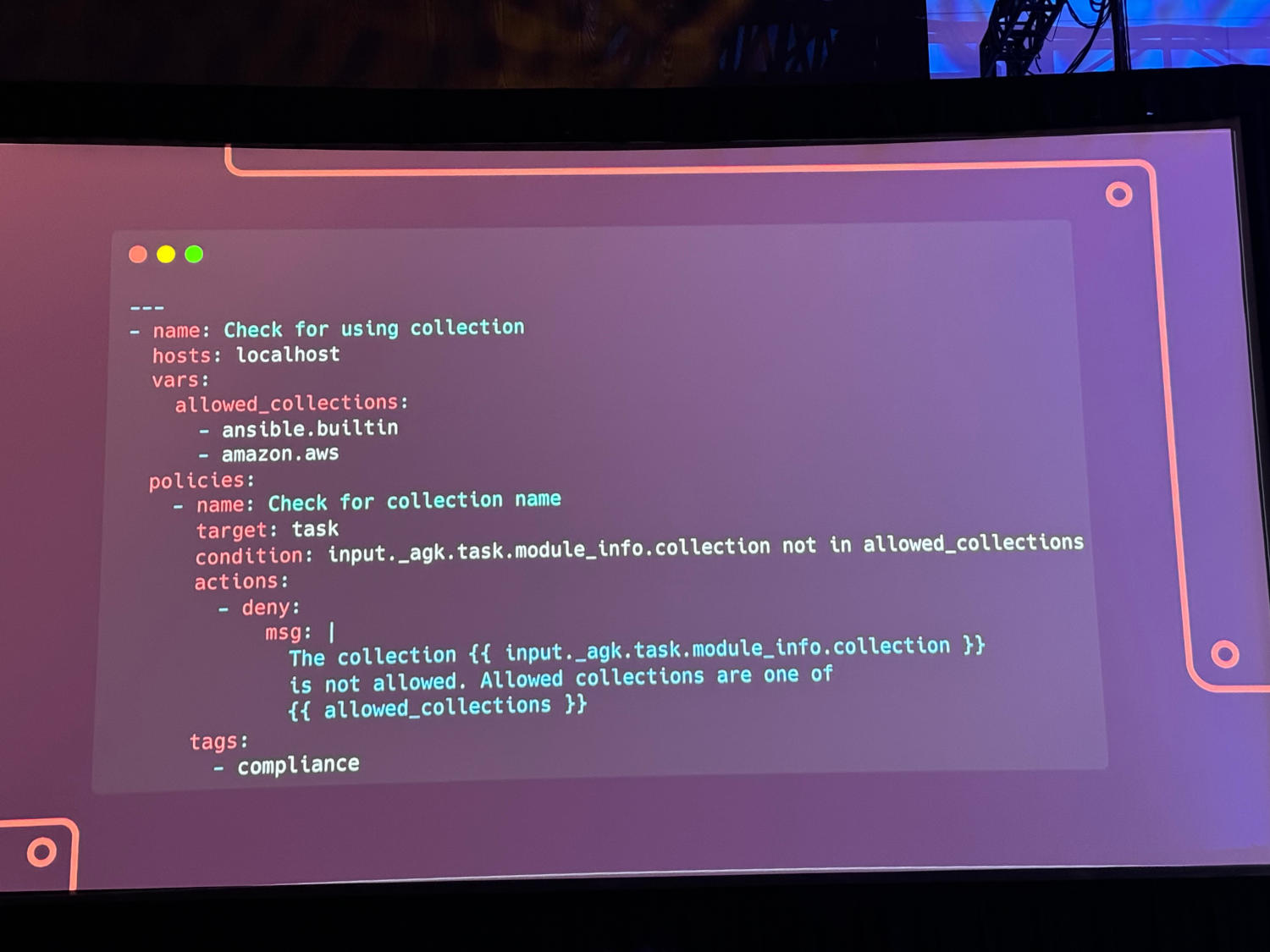
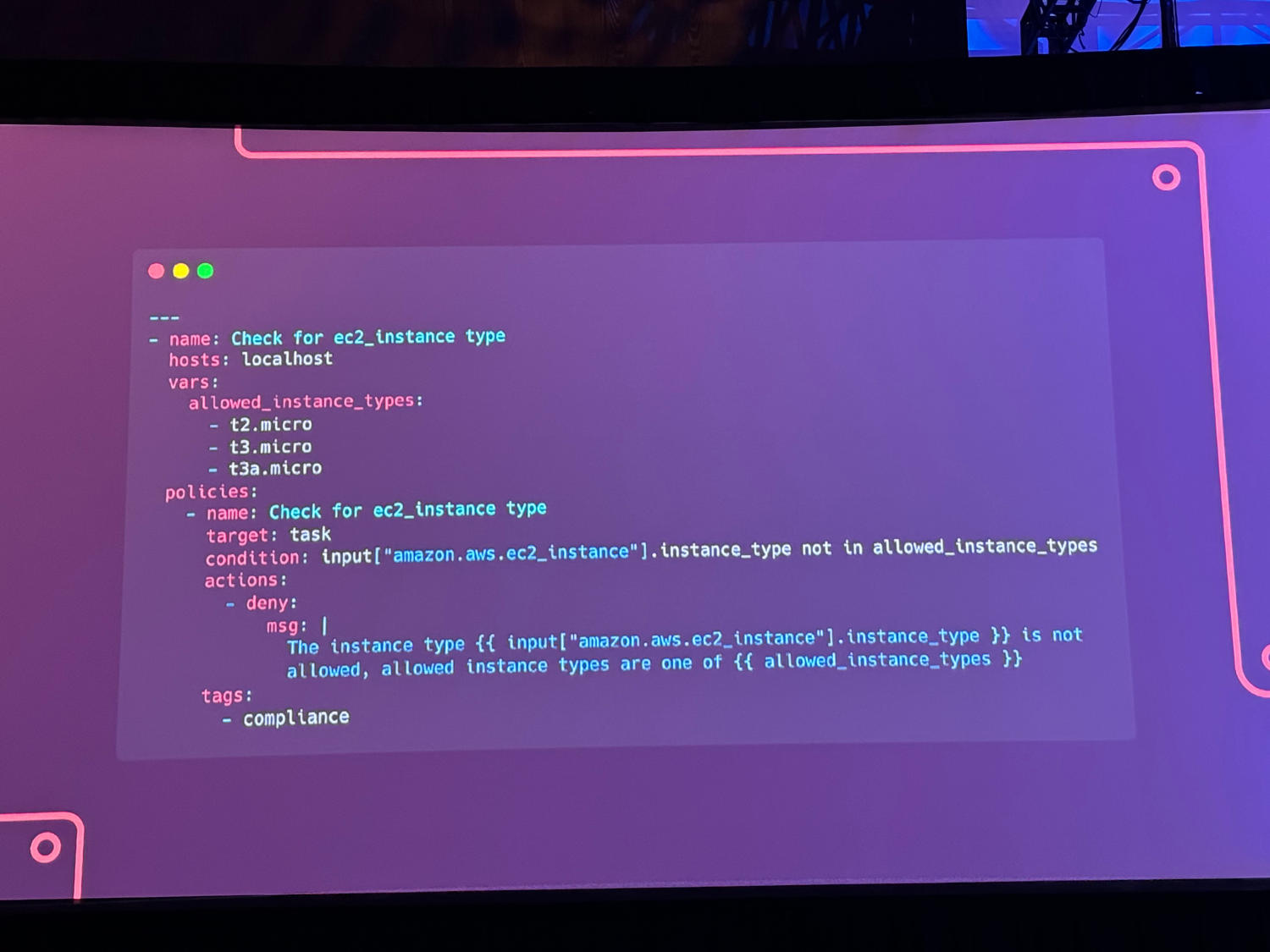
Ansible development tools
There was also news regarding the development tools. With ansible-creator I have learned a framework for easier creation of Ansible content. This offers extensive templates for collections, playbooks, CI/CD pipelines and unit tests.
The Ansible Development Tools is a Python meta package that installs all development tools and required dependencies. The versioning is based on the current date in order to quickly identify outdated installations.
The tool for static Ansible code analysis, ansible-lint, has been extended by the parameter --fix and can thus automatically correct some common errors. A new version of the ansible-builder allows easier creation of execution environments for AAP or the upstream AWX.
With community-ansible-dev-tools, a container image was introduced that is based on Fedora and contains all Ansible development tools. An optional Visual Studio code integration allows easy development of Ansible content without the tedious configuration of tools. This should be particularly interesting for Immutable Linux distributions, such as Fedora Silverblue.
In the GitHub marketplace there is a ready-made CI/CD development pipeline with ansible-content-actions. This can automatically test code and create changelogs and release notes. This should be very useful in combination with repositories linked to Ansible Galaxy.
Image Mode for RHEL
Another highlight for me was the announced installation variant Image Mode for RHEL. In contrast to conventional installations with RPM repositories, technologies are used here that are already used in software development. This means that complete installations can be carried out on the basis of a container file - for example via a CI/CD pipeline. Dedicated tools such as Red Hat Satellite or Ansible are no longer required for system configuration.
The central component of this approach is the bootc tool, which can boot and update conventional OCI containers, such as those used by Docker and Podman, on standard hardware and file systems (XFS, ext4). However, the big difference to conventional containers here is that a kernel must be included in the image.
Conventional RPM packages cannot be installed, some core components are installed via OSTree - OCI images can be used for other requirements. Consequently, updates conceptually require a reboot and are displayed as a new version in the GRUB boot loader. This is a feature that NixOS users will be familiar with. In general, NixOS served as one of the sources of inspiration, as an interview revealed and some bootc commands also suggest:
1# bootc status
2# bootc switch
3# bootc upgrade
4# bootc rollback
Project Bluefin is a Linux workstation aimed at developers that uses the same technical foundation. Here, the GNOME desktop is combined with Flathub, GPU drivers and useful OCI images. There are ready-made ISO images for x86 computers, a version for Apple hardware is in the works.
Both tools are considered Technical Preview and should therefore not yet be used in production.
Fedora ELN and CentOS Stream 10
The presentation "What's Next in Fedora's Innovation Pipeline" by Stephan Gallagher (Principal Software Engineer, Red Hat) and Davide Cavalca (Production Engineer, Meta) was also very exciting. It was discussed that Fedora primarily stands for innovation, while RHEL is used for stability. Insight was provided into the RHEL release process, in which experimental features and some Fedora dependencies have to be removed. Packages also need to be split between the BaseOS, AppStream and CRB repositories.
CentOS Stream serves here as an intermediate stage between Fedora and RHEL - during the lifetime of a RHEL release, it is regarded as the development version of the next minor version. Before this approach was established - for example with the RHEL 9 release - it took a dedicated development team 9 months to port the Fedora code.
This project was considered too time-consuming and complex, as Red Hat claims to release new major versions every 3 years. This is remedied by the use of Fedora ELN, which emulates the RHEL development process on the Fedora Rawhide code base. Rawhide is the current Fedora development version and contains the latest packages. This approach allows impacts, such as bugs or new CPU architecture requirements, to be identified early for later RHEL versions. Recently Fedora 40 was released, which forms the basis for the upcoming RHEL 10. The effort of the code migration due to the new approach was stated to be only one month.
Meta uses CentOS Stream in production and Fedora ELN in the development environment to make updating to new major versions as painless as possible. CI/CD pipelines are used for this and updates are installed automatically in the test environment in order to test the effects at an early stage. There are also plans to use CentOS Stream 10 productively before the end of 2024.
One of the reasons I found the presentation interesting was because it showed that CentOS Stream can be used in production. In addition to Meta, CERN also uses the distribution on a large scale. In German-speaking countries, many customers vehemently hold on to the myth that this distribution is unstable - refreshing to see that this is not the case.
Networking
Once again, I had the most fun meeting people that are otherwise not so easy to meet. So I had the opportunity to talk to Neal Gompa and Leonardo Gallego (Ansible Catalyst and Technical Marketing Manager, Red Hat) after our paths had already crossed on the internet 😀.
In the Red Hat Event Guide app, contact details could be exchanged via the QR codes printed on the participation badges and there was also an exchange on social media via the hashtags #RedHatSummit and #RHSummit.
I was very pleased that we were able to conduct interviews with some experts again. We spoke with Craig Brandt (Senior Principal Product Manager Ansible, Red Hat) about the Ansible Automation Platform 2.5, while Eric Hendricks (Technical Product Marketing Manager, Red Hat) gave us his assessment of RHEL Lightspeed. With Matthew Miller (Fedora Project Leader and Distinguished Engineer, Red Hat) we talked about the current developments of the Fedora project. We learned details about Image Mode for RHEL from Stef Walter (Senior Director Linux Engineering, Red Hat). The exchange on maintaining communities with Carol Chen (Open Source Community Architect, Red Hat) was also very nice.



Beside the conference
If time permits, exploring the city is recommended. Denver was once a gold mining metropolis and is the capital and most populous city in Colorado. Located in close proximity to the Rocky Mountains, there are numerous outdoor activities. Culturally the city offers the impressive Denver Art Museum as well as several theaters and an opera house.
Red Rocks Park is an impressive sandstone mountain park including an amphitheater. Nearby is the Dinosaur Ridge Trail - one of the world's most important dinosaur fossil sites, where well-preserved traces can be viewed. The Rocky Mountain National Park offers breathtaking views - an absolute highlight!









Conclusion
I really enjoyed the conference again - especially the exchange with other participants and community members had an absolute added value for me.
Personally, I would have liked to see more variety of topics away from the AI trend - but I consider the InstructLab announcement and extended Ansible Lightspeed functions to be important. I find the Image Mode for RHEL technologically exciting and am looking forward to trying it out. I'm no less excited about the new AAP version and I'm also looking forward to the first CentOS Stream 10 release. All in all, there was plenty of exciting news. I find it a bit of a shame that there were no announcements regarding Red Hat Satellite. The current version 6.15 was recently released - I would have been interested in a preview of upcoming functions.
I'm looking forward to the next event - Red Hat has already announced that it will take place in Orlando.