Red Hat Summit 2025

From 19.05 to 22.05 the Red Hat Summit took place contrary to the first announcement again in Boston and not in Orlando. The conference again centred on announcements and current developments from within the company's own ranks. Approximately 7,000 participants attended the event.
On the occasion of the Red Hat Summit 2025, a special episode was published in the Urlaub im Userspace podcast.
Location
The event was held in the almost 5 hectare Boston Convention & Exhibition Centre. There was plenty of space for the 457 presentations, workshops and hands-on labs. Compared to previous years, the Red Hat Event Guide app was revised and now also offered indoor navigation. It was also essential to plan your own agenda in the form of a calendar in advance, as particularly popular sessions were usually fully booked before the start of the event. This year, however, we were reminded several times by e-mail to plan your own agenda.
In the exhibition area there were community stands (including Ansible, Foreman, Fedora) as well as numerous manufacturers who answered questions and also presented new product versions. There were plenty of opportunities for interaction, e.g. through demos and games.

The exhibition area was pleasantly large and could be easily accessed during the conference days. The usual swag on offer included shirts, pins and stickers. Visitors could choose between a personalised conference backpack or a tote bag free of charge - provided they waited long enough.



Keynotes
Unfortunately, the omnipresent AI ✨🚀 hypetrain is still on the move - even outside the Red Hat bubble. Already in the first keynote (Enterprise AI & modern infrastructure), Matt Hicks (President and CEO, Red Hat) emphasised Red Hat's continued focus on open source solutions and communities around AI. In addition to spongy pitches, the agenda also included numerous field reports on Red Hat AI and OpenShift AI. Interestingly, there were also specific software projects that were mentioned. For example, Red Hat AI Inference Server, a new software for the efficient execution of different LLMs, was presented - the corresponding upstream projects are llm-d and vLLM. Another new tool from Red Hat is Docling, which is intended to facilitate the mass processing and conversion of documents in preparation for GenAI.


Two buzzwords I hadn't heard before were Agentic AI and MCP (Model Context Protocol). MCP is an open-source standard protocol for communication between applications and AI models - like a kind of USB-C port for AI applications. This allows those applications to communicate with each other and request and verify further information across contexts (e.g. verify a proposed solution via a knowledge base). Agentic AI refers to applications that implement MCP and thus simplify interaction with other applications.
Another intensively discussed product was OpenShift Virtualization. In addition to numerous reports of successful migrations, there were also some criticisms of Broadcom.


Red Hat Enterprise Linux 10
Surprisingly, the RHEL 10 installation media already appeared a few days ago on the internet - usually this step only takes place during the conference. In this case, the conference was moved to a different location and date - but the release dates remained the same. The changes compared to RHEL 9 are hardly surprising thanks to the previous public beta. The numerous version updates include:
- Linux 6.12 (instead of 5.14)
- glibc 2.39 (instead of 2.34)
- OpenSSH 9.9 with post quantum security
- Python 3.12
- PostgreSQL 16
GNOME is available in version 47 - Redis has been replaced by Valkey 7.2. Cockpit has been supplemented with add-ons for cluster operation (pcsd) and file management. Ansible System Roles new additions include automatisms for sudo and AIDE.
Red Hat announced that it will enable an in-place upgrade from RHEL 9.6 to 10.0 - older releases must first be upgraded to RHEL 9.
The release notes also contain numerous deprecations and removals this time. For example, 32-bit packages (i686), X11 (and Motif!) and the RHEL Resilient Storage Add-On are a thing of the past. VNC has been replaced by RDP and is also no longer available for remote installations.
Numerous applications will only be available as Flatpak in the future, including
- GNOME Evolution
- LibreOffice
- Inkscape
Due to the desktop update, some GNOME applications have also been replaced, for example:
- Eye of GNOME became Loupe
- gedit gives way to GNOME Text Editor
- Cheese has been replaced by Snapshot
- Papers is an Evince fork developed in Rust with GTK4 support
Pipewire is the successor of PulseAudio, power-profiles-daemon is dropped and is now part of the Tuned service (tuned-ppd).
CGroups of the first generation are no longer available, runc and SquashFS have been marked as obsolete. The Predictable Network Interface Device Names introduced in RHEL 7 can no longer be disabled by the kernel parameter net.ifnames=0.
Another new feature, which is also included in RHEL 9.6, is the snapshot manager snapm. This makes it easy to create and manage LVM2 snapshots. In combination with the Boom Boot Manager, boot entries can also be created for these. This means that failed maintenance work can be quickly undone - bare metal installations in particular should benefit from this.
One technical preview is particularly worth mentioning: XFS now supports the shrinking of file systems, provided there is no metadata or actual data in the storage area to be removed.
This is clearly an highlight for me, as I always miss this function. In system administration, you always have to deal with temporarily increased storage requirements - and XFS has not been able to score points here so far. Other file systems such as ext4 can usually be expanded online and at least shrunk offline. I am pleased that this will change soon.
RHEL Lightspeed
The AI assistant presented for the first time last year has been revised. Designed as a command line application, it uses a specially trained IBM WatsonX-LLM, which is provided as a SaaS application. A valid RHEL subscription is also required for this. As the submitted queries are used for further training, this feature should be used with caution.
The assistant is primarily intended to provide support for questions and troubleshooting relating to the operating system, but it should also be useful for analysing log files.
The client is developed in Python and can be conveniently installed via pip. It is executed via the command-line-assistant command, with c a simple alias was created. I am afraid that typing errors (e.g. c instead of cd) will be the reason for frequent executions. The client can also be used directly in pipelines, for example to send log files to the model.
Technically, I find the solution quite interesting - however, we should not forget to censor potentially sensitive information in advance. I would welcome it if the underlying language model could also be operated on-premises.
RHEL Image Mode
A promising technology that was already announced last year is RHEL Image Mode.
Compared to last year, the technology has now matured further and could be tried out in hands-on labs. A dedicated documentation describes its use - also in security-critical environments.
The concept still stands for an immutable RHEL in the form of bootable OCI containers. This allows applications and systems to be packaged and rolled out automatically in the form of CI/CD pipelines - from edge devices and notebooks to Kubernetes clusters.
Technically, classic OCI images and OSTree repositories are used. The boot loader used can boot container images and therefore versions. As with other immutable Linux distributions, the root file system can be accessed read-only. Files below /etc are merged between the container image and the local file system, whereby local changes have priority. /var, on the other hand, contains only local data - files stored there in containers are therefore ignored. This means that application data (e.g. website content) may have to be saved in other folder structures.
Red Hat Satellite 6.17
Satellite 6.17 has also been released in advance. The new version is based on Foreman 3.14 and Katello 4.16 and supports RHEL 10 as well as RHEL Image Mode. When deploying new machines, Secure Boot and IPv6-only networks are supported.
Another new feature is the distribution of Flatpak content - for the time being, however, only via the command line. Also, only the Red Hat and Fedora-Remotes are currently supported - the popular Flathub is to follow soon.
A technical preview allows multiple Content Views (CV) to be assigned to a host. This is not yet possible, but a common alternative is to combine several CVs as a Composite Content View (CCV) - a concept that still overwhelms users today:
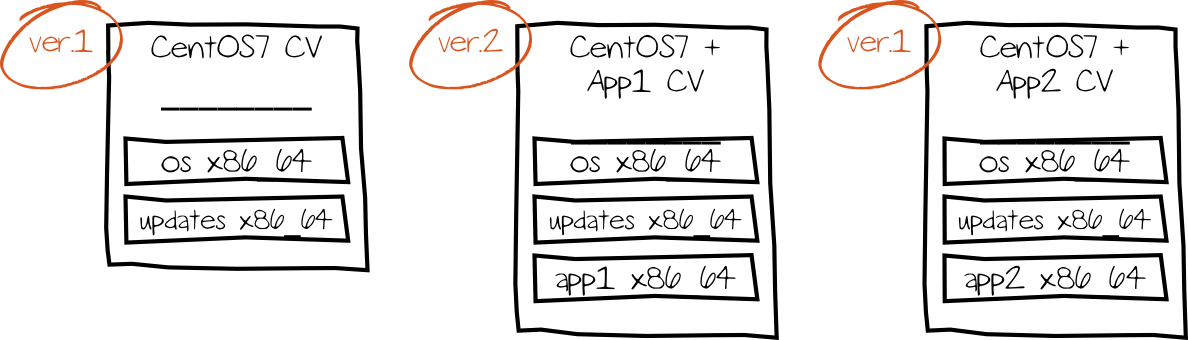
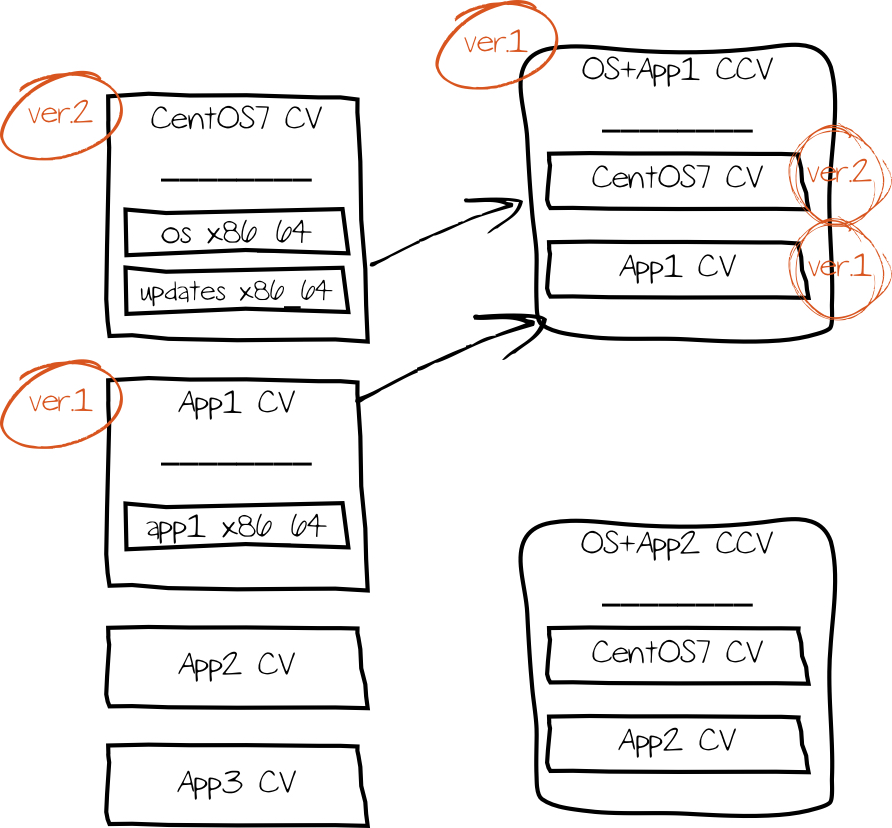
The feature can currently only be used via the command line - subsequent changes made to the CV via the web interface overwrite the settings again. The next Satellite version should also make the configuration accessible via the web interface.
Red Hat Insights Advisor
Another highlight is that Red Hat Insights Advisor can now be run locally on the Satellite host. Red Hat Insights is a comprehensive SaaS service that provides customers with a comprehensive insight into their own infrastructure in order to proactively mitigate potential risks. Vulnerabilities, misconfigurations, non-compliant best practices and malware are listed. A management-ready interface clearly summarises metrics - these findings can be often automatically mitigated at the click of a mouse if desired.
This service consists of a series of networked services that could not previously be operated on-premises - this is now changing. This should be of particular interest to public customers or those with a high understanding of data security. Previously, meta information (installed packages, possibly censored host name and IP address) of registered systems was stored at Red Hat.
With Red Hat Satellite 6.17, the first service can now be executed locally as a Podman Quadlet, as I was able to find out in a hands-on lab. This is a stateless Python web application that communicates with Satellite via a REST API. No system information is stored in the container - the current set of rules is available in the form of Python code. Information reported via the Insights client is analysed via the application and recommended measures are reported back to Satellite. These measures can include, for example, the application of specific configurations. The container image is updated monthly as an RPM package - so nothing stands in the way of its use in airgapped environments.
The functionality can be conveniently activated and deactivated via satellite-installer, the previous insights-client can continue to be used.
Roadmap
Satellite 6.18 will be released next November. The biggest change is likely to be the provision of the Satellite server as a container. Red Hat is thus making a radical change to the type of installation - analogous to the Ansible Automation Platform and SUSE's Multi-Linux Manager.
Technically, Podman Quadlets will be used again - it is still unclear which services will be outsourced to dedicated containers. When asked, Satellite is not intended to be a microservices application - however, the company is open to a later deployment on Kubernetes. Technically, it is also possible to run Satellite on non-RHEL distributions - but without any claim to support. At this year's CfgMgmtCamp 2025, Evgeni Golov gave an exciting insight into the developments to date.
With Insights Vulnerability, another Insights service is to be run locally. This synchronises CVE information and other best practices in order to increase the security of registered systems.
Satellite 6.19** is planned for the upcoming May 2026. In this version, Capsules will also be executed as containers. The next Insights service, Insights Compliance, will be available locally. The RBAC functionality already familiar from Ansible Automation Platform 2.5 and other Red Hat services is to be integrated. This allows access authorisations to be defined more conveniently and clearly.
Satellite is not immune to AI technology either - MCP is to be implemented for the use of Agentic AI. This should be particularly useful if Satellite is used in combination with Ansible Lightspeed or RHEL Lightspeed.
More hands-on labs
The numerous hands-on labs, in which numerous technologies and products could be tried out, were once again an absolute added value. Experts and sometimes even the responsible developers were available to answer questions.
In two RHEL 10 labs, visitors were able to try out old and new functions - including the new Image Mode. In particular, a lot of work was done with the bootc command to create, boot and update containers. An ISO file was also created to automatically install a VM with a container. The concept seems well thought out and is convincing - NixOS users will probably recognise the syntax.


No less interesting was a security lab, in which I was able to try out SELinux and auditd as well as fapolicyd. I had never used the latter before. It is remotely similar to AIDE, but reacts proactively instead of reactively. It maintains a database of installed files with access patterns and restrictions - violations can be actively prevented. This effectively prevents manipulated files from ending up on a system and being executed.
In the Ansible Automation Platform 2.5 lab, I was finally able to try out the new centralised web interface. It combines the previously dedicated web interfaces of the Automation Controller, Automation Hub and Event-driven Ansible Controller. Centralised navigation makes it easier to use the individual components - dedicated tabs are no longer required.
To counter supply chain attacks, Ansible has been offering the ansible-sign command for some time to sign Ansible content. This technique was tested in a lab to protect stored playbooks from unwanted changes. Once activated, content is only executed if a valid GPG signature is present. This means that a potentially shijacked Git repository can be mitigated as an attack vector.
Ansible
There have also been numerous innovations to the popular Infrastructure as Code tool.
ansible-core
Version 2.19 of the Ansible core is accompanied by some breaking changes. For example, the Python implementation paramiko of the SSHv2 protocol has been discontinued - a new SSH plugin is mentioned as a replacement, which also replaces sshpass for interactive password queries. SSH agents are to be supported in the future.
Jinja2 is to support lazy rendering in the future and thus be executed faster overall. In the event of errors, there should also be more precise line information and potential causes of errors. So far, the information here is still a little thin, which makes it difficult for new users in particular to get started.
The previous version 2.18 is expected to be supported until May 2026 - so developers still have some time to adapt their own code for the new version.
Ansible Automation Platform
The future version 2.6 of the in-house configuration and orchestration solution is scheduled for release in September 2025. The current version 2.5 will be supported at least until September 2027, 2.4 will receive two more years of Extended Life Cycle Support (ELS) in June 2026.
The Policy Enforcement feature already announced last year will be available from July. This function can be used, for example, to ensure that only approved Ansible collections or parameters (e.g. maximum instance sizes when creating new VMs) are used.
With redhat.ai and infra.ai there are two new Ansible collections for Day 1/2 administration and the operation of Red Hat AI infrastructure.
The first results following the acquisition of HashiCorp by the parent company IBM were also visible. A better integration of Vault and Terraform in Ansible Automation Platform was demonstrated. Terraform components and dependencies are now visible in workflows, and Vault can now serve as a single source of truth for secrets of any kind.

Ansible Lightspeed
Compared to last year, the GenAI assistant has been further refined and can now also explain existing Ansible code. All in all, the model trained with verified and public Ansible content no longer hallucinates. This is also achieved by the fact that Ansible Lightspeed now links to the official Ansible documentation and can thus verify proposed code.
The wizard can currently only be installed as an OpenShift operator - later it should also be possible to install it as a classic Podman setup. Packaging as an RPM package is not planned.
Red Hat Offline Knowledge Portal
Another introduction I initially thought was an April Fool's joke: the Red Hat Offline Knowledge Portal (RHOKP). Specifically, it is a locally executable copy of the complete Red Hat Knowledge Base - starting with RHEL 4.
Technically, an almost 7 GB Podman container image for the x86_64 and aarch64 architectures is used here. This runs a small web server with a static website - an integrated Elastic Search Engine also makes it easier to find information.
This solution should be particularly relevant if you are travelling in airgapped environments or commute frequently and therefore do not have a reliable internet connection. The team behind it spent two years converting and formatting old documentation so that it fits into the look and feel of the knowledge base and is presented in a meaningful way.
The offer was rounded off with a Survival Kit bag, which contains a notebook, pockets for small items and a multifunction pen. This combines a whole host of functions: Torch, screwdriver, biros and a touchscreen pen. The bag also comes with a branded USB stick, although it is empty. And there is a good reason for this: the RHOKP is only available to customers with a valid satellite subscription.
The documentation describes the use.

Networking
For me, one of the main reasons for attending international conferences is the exchange with experts and developers. Despite the size of the event, it was once again possible to make contacts and submit feedback and questions to the individual product teams very easily.
In the Red Hat Event Guide app, contact details could be exchanged via the QR codes printed on the participation badges and there was also an exchange on social media via the usual hashtags #RedHatSummit and #RHSummit.
Conclusion

For me, the conference once again had added value - the exchange with other participants and project members in particular was very informative.
I would have appreciated more technical news and fewer buzzwords in the keynotes. I understand that AI is an omnipresent topic - but the sessions would have benefited from more tangible content. Admittedly, I am probably not the target group for these presentations.
I find the technical innovations of RHEL 10 and Satellite 6.17 very exciting. In particular, I find the on-premises insights services refreshing at a time when manufacturers are increasingly pushing their customers into SaaS offerings.
Red Hat announced that the next conference will take place from 11.05 to 14.05.2026 in Atlanta (Georgia).