Cisco SG 300: configure Port Security with MAC filtering
If you own a Cisco SG-200/300 switch you are lucky to configure Port Security and MAC filtering. The advantage of this is that you are able to define which MAC addresses may establish connections on particular ports. Other devices will not be able to access the network - which is a good idea especially for public network sockets.
Configuring this mechanism is quite easy - if you know the particular steps. In this example one device is configures to access a particular network port - but it is also possible to enable more than one device for accessing ports. It is a good idea to connect all devices that need to be able to establish connections to the switch while configuration.
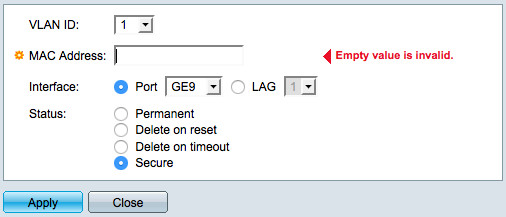
First of all static MAC assignments need to be configured for all affected devices/network ports. This can be done using a dialog. You will find this dialog by browsing the menu underneath the items "MAC Address Tables > Static Addresses".
In this example the dialog is filled like this:
- MAC Address: (device MAC address)
- Interface: Port GEx (appropriate network port)
- Status: Secure (make sure to use this!)
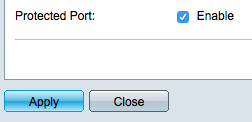
After all required MAC addresses have been configured on the switch (it is also possible to configure more than one) switch port "Protection" needs to be enabled for the appropriate switch port (IMHO a better description would have been great, Cisco!). This setting can be configured by browsing the menu underneath "Port Management > Port Settings". During the port configuration the checkbox "Protected Port" needs to be set to "Enable". After that the the port table column "Protected Port" should contain the value "Protected":

Afterwards Port Security needs to be configured for that affected switch ports. This configuration is made by editing the appropriate switch port underneath the menu "Security > Port Security" editiert. In this example the dialog is filled like this:
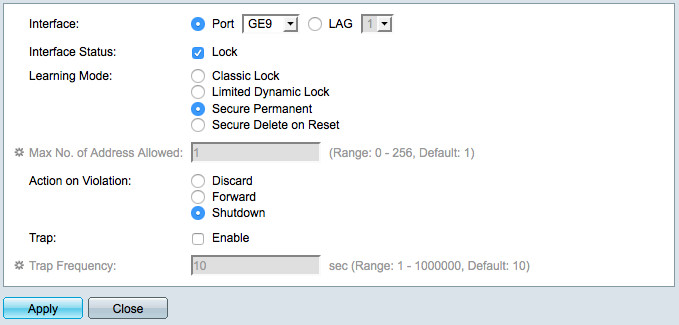
- Interface Status: Lock (otherwise Port Security isn't enabled - sounds strange, I know)
- Learning Mode: Secure Permanent
- Action on Violation: Discard (if you want to drop packages of other hosts) or Shutdown (if you also want the network interface to be shut down)
If you select the setting "Shutdown" the network interface is shut down after the first "unknown" network device is connected. This means manual tasks are necessary to re-enable the network interface but this offers much greater security in case of brute-force attacks (various software might fake MAC addresses).
Afterwards Port Security and MAC filtering is implemented - I highly recommend to check the functionality. Often a checkbox is missed and the lock is not working which might result in a major security vulnerability.